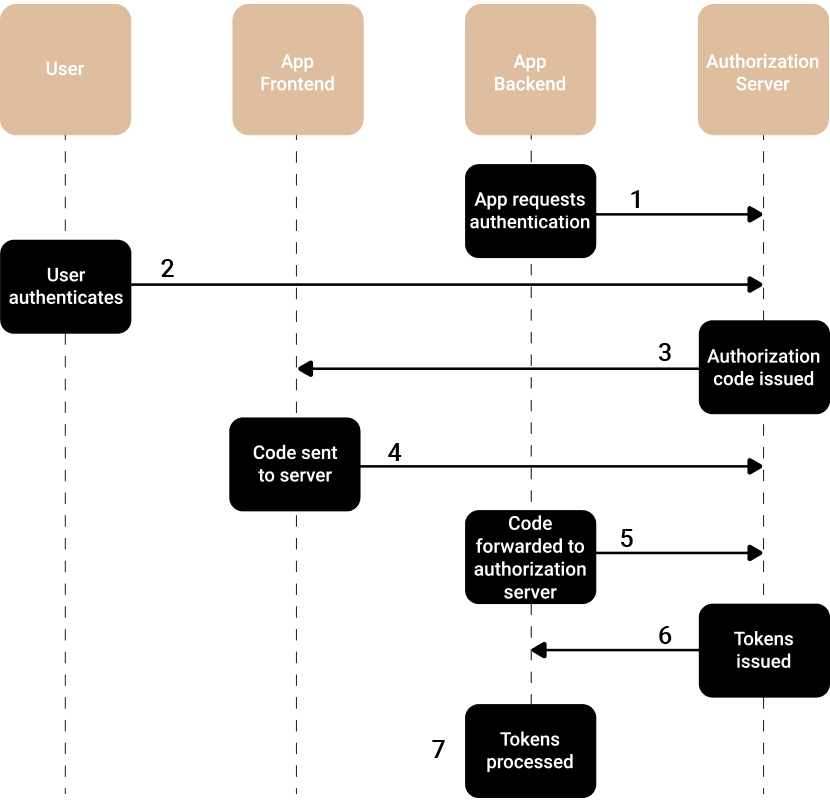
The App Backend attempts to access a resource that requires authorization that it does not have. It redirects the user to the authorization server for authentication.
The Authorization Server authenticates the user by asking for their login credentials. The server determines if the user should be granted or denied their request.
If the User is determined to be authentic, an Authorization-Code is issued and returned to the App Frontend. This code is used to retrieve an Access-Token from the Authorization Server.
The retrieved Authorization-Code is sent to the App Backend.
The App Backend makes a POST request to the Authorization Server, containing its Client-ID, Client-Secret, and Authorization-Code.
The Authorization Server verifies the key, secret and code, and issues an Access-Token and Refresh-Token.
The App Backend receives and processes the Access-Token. The Access-Token is then kept in the App Backend, which can request resources on behalf of the App Frontend without exposing the token itself.
| Item | Description |
|---|---|
| Client-Id | The integrators key to exchange an Authorization-Code for an Access-Token (unique for the application and connected to the Client-Id) |
| Client-Secret | The integrators key for making requests (unique for the integration and connected to the Client-Id). |
| Authorization-Code | Generated when the customer authenticates and approves the connection between their account and your application. Expiration time: 10 minutes. |
| Access-Token | Token with limited lifetime used by your application when making API requests on behalf of a user. Expiration time: 1 hour |
| Refresh-Token | Long-lived token used to generate a new Access-Token once the old one has expired. Expiration time: 45 days |
When a user performs the authentication we generate an Authcode (valid for 10 min) which is sent to the integrator through the redirect URL.
The integrator receives the Authcode and activates it. In response to the activation, we generate an Access Token (valid for 1 hour) and a Refresh Token (valid for 45 days).
The integrator uses the Access Token to make calls to our API. These calls do not affect an expire date, neither for Access-Token nor Refresh-Token.
When the Access Token expires after one hour, the integrator uses its Refresh Token to obtain a new Access Token. When this is generated, a new Refresh Token is also created. The old Refresh Token then becomes invalid.
The Refresh Token is valid for 45 days and within this time a new Access Token can be generated. If the Refresh Token has expired, the user needs to re-authenticate and we start again at authentication.
See our comprehensive documentation regarding the Fortnox API.
Approximately half a million customers are waiting for your integration at our Integrations page.